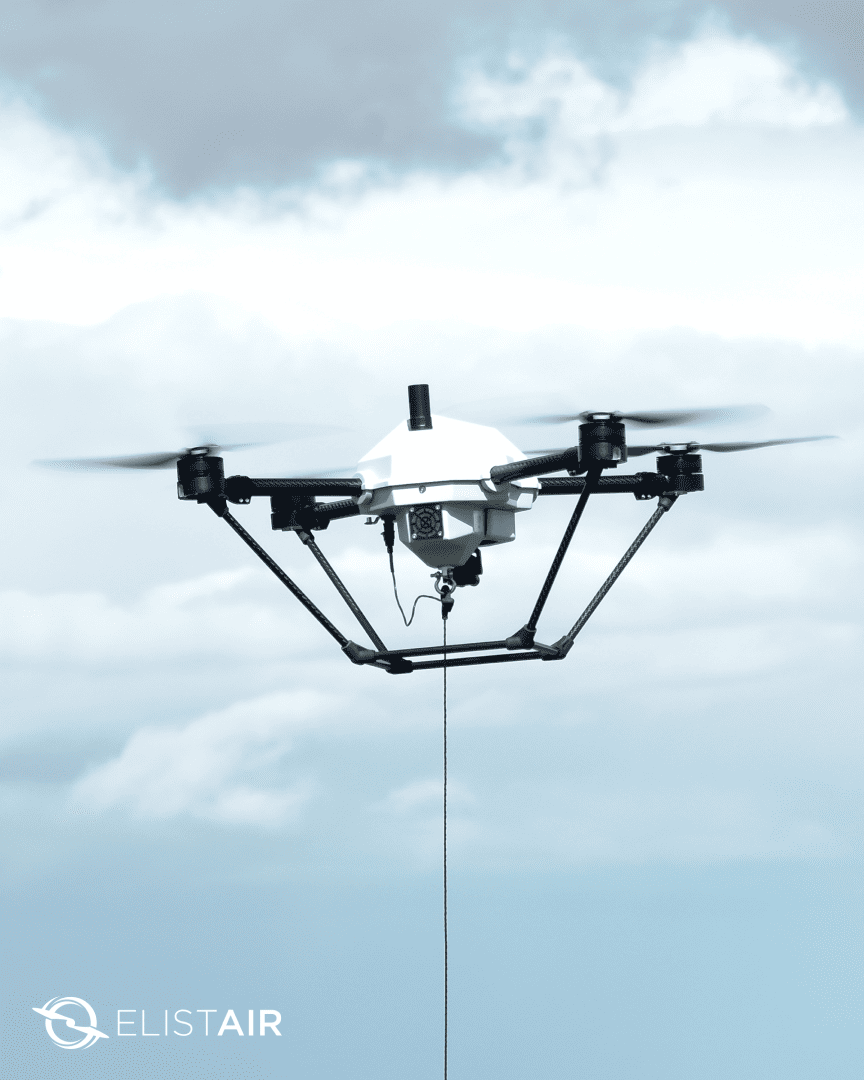
Tethered UAV Systems: Use Cases and Recommandations
Key Operational Use Cases for Tethered UAV Systems
Tethered UAV systems have specific use cases where their strengths – persistence, secure comms, and quick deployment – provide an operational edge. Below are four primary applications relevant to military and border ISR professionals, each aligning with lessons learned and current doctrine.
Forward Operating Base Protection
At forward bases and outposts, maintaining constant surveillance of the surrounding area is vital to early warning and defense. Tethered drones excel at this mission by acting as stationary guardians hovering over the base perimeter day and night. They can detect approaching threats such as insurgent movements, vehicle-borne improvised explosives, or infiltrators, and do so continuously without gaps in coverage.
NATO forces have employed tethered UAVs at forward operating bases (FOBs) to bolster force protection – a practice born from the protracted base-defense needs in conflicts like Afghanistan and now refined with smaller drones. Persistent aerial overwatch can spot suspicious activity beyond the wire and track enemy reconnaissance teams or drones before they get close. Tethered drones have proven excellent at detecting and even deterring attacks and intrusions in FOB environments, as continuous surveillance makes it far harder for adversaries to achieve surprise.
Doctrinally, commanders are beginning to treat tethered ISR as an integral part of base defense plans, akin to having an always-active sentry in the sky linked directly into the base security network. The emphasis is on rapid deployment (a tethered drone can be launched in minutes when a base is established) and seamless integration with ground surveillance radars and sensors, creating a layered defense.
Mobile Convoy Escort and Unit Surveillance
Tethered UAV systems can be mounted on or integrated with vehicles – from armored personnel carriers to unmanned ground vehicles – providing on-the-move reconnaissance for convoys and maneuver units. This mobile escort role effectively gives moving forces their own aerial lookout that travels with them. A vehicle-mounted tethered drone can rise above treelines, buildings, or terrain masking to scout ambushes ahead of a convoy and extend communications in areas where line-of-sight is poor.

could halt briefly to deploy the tethered quadcopter or even deploy it while on the move at slow speed, to get a 360-degree view of the area. This capability was demonstrated in Germany’s recent trial, where an unmanned ground vehicle equipped with a tethered drone provided continuous ISR feed to troops on the move.
The doctrinal implication is that tethered drones will be part of future maneuver formations, improving situational awareness during marches and maneuvers. Units need to train on using these drones dynamically – e.g. when to launch or retrieve them during an operation – and how to fuse their live feed with other reconnaissance reports.
Escorting high-value convoys (such as logistics or command columns) is another scenario where persistent overwatch from a tethered UAV can drastically reduce surprise attacks or improvised explosive device (IED) threats. Rather than relying solely on sporadic helicopter or satellite coverage, the convoy carries its own constant recon asset.
Border Surveillance and Perimeter Security
Tethered UAV systems are highly suited for border security missions, whether operated by the military or other security agencies, because they can cover wide areas continuously and respond quickly to repositioning needs. By their nature, borders and sensitive perimeters (like demilitarized zones or ceasefire lines) are extensive and often in remote regions where building permanent surveillance towers is impractical.
Tethered drones, especially those that are vehicle-portable, can rapidly deploy to key locations and provide aerial surveillance for as long as needed. They have already seen successful use at border checkpoints and remote border sectors, monitoring for illegal crossings, smuggling, or incursions.
A tethered drone’s high vantage point and persistent stare capability make it effective at detecting movement along border fences or in difficult terrain, day or night, and even at monitoring large crowd activities during border demonstrations or refugee flows.
In Europe, for instance, these systems could augment EU border agency operations by filling surveillance gaps along expansive frontiers. Many countries also utilize tethered drones for critical perimeter security at strategic sites like airports, ports, or military installations – essentially a similar application to border overwatch but focused on a specific facility’s perimeter.
Because tethered UAV systems can be relocated and set up with relatively minimal logistic footprints (especially compared to large aerostats or permanent masts), commanders appreciate their flexibility in crises: a tethered drone can be dispatched to a threatened border sector or a vulnerable site at short notice to establish immediate ISR coverage. Doctrine is evolving to include such systems in border surveillance plans and as part of “ISR surge” capabilities during heightened tensions, where additional persistent eyes are needed on critical sectors.
Tethered UAV Systems for Critical Infrastructure Overwatch
Beyond battlefield uses, militaries and security forces are using tethered drones to safeguard critical infrastructure and high-value installations – from forward-deployed Patriot missile batteries and radar sites to civilian power grids and communication hubs. The persistent overwatch provided by a tethered UAV can detect and track potential threats such as small aircraft (including weaponized drones) or ground intruders approaching key infrastructure.
For example, a tethered drone positioned at an airbase or headquarters can monitor the surroundings out to several kilometers, giving early warning of any incoming drone swarms or special forces teams. In the context of modern NATO and European defense, where infrastructure like fuel depots, satellite uplinks, or supply hubs could be targets of sabotage or air attack, having an organic ISR overwatch asset adds a layer of protection.
Tethered UAV systems carrying electro-optical/infrared cameras or even compact radar can identify threats that ground patrols might miss, especially at night or in complex terrain. Additionally, these drones can serve as communications relays at critical sites, ensuring that if other comms are disrupted, the tethered system can bridge radios or networks over the horizon. Since tethered drones operate on continuous power, they are ideal for standing watch over infrastructure for days or weeks on end (rotating units as needed).
Commanders in charge of rear-area security or homeland defense are advised to include tethered ISR assets in their protection schemes for vital assets – much like militaries have long used stationary guard towers or aerostats, but now with far greater flexibility. The key doctrinal change is to view critical infrastructure protection not just as a static guard mission, but as one that can leverage modern ISR technology to stay one step ahead of potential attackers.
Doctrinal Recommendations for Commanders and Planners
Integrating tethered UAVs into ISR doctrine requires deliberate planning and adjustments to tactics, techniques, and procedures. Below are specific recommendations for commanders and ISR planners to maximize the effectiveness of tethered drone systems:

Incorporate Tethered UAV systems as Organic Unit Assets
Treat tethered ISR drones as an organic part of unit equipment at the battalion or brigade level (and their equivalent in other services). Much like night vision devices or radar sets, they should be in the commander’s toolbox for ISR tasks.
Commanders should plan for tethered drone deployment in operational phases – e.g., launching a tethered UAV immediately when establishing a forward command post or defensive position to gain instant overwatch. This means assigning trained drone operators in units and accounting for tethered systems in unit TOE (Table of Organization & Equipment). Early adopters like the U.S. Army are already moving in this direction, aiming to field tethered drones to armored units and other formations as standard gear.
Develop Tactics for Contested Environments
Given the demonstrated resilience of tethered UAV systems against jamming and detection, doctrine should outline their use in electromagnetically contested scenarios. Planners should incorporate scenarios where tethered drones provide ISR when GPS is knocked out or radio links are unreliable. For instance, during exercises, simulate heavy EW conditions and practice relying on tethered drone feeds as the primary source of local intelligence.
Additionally, ensure tethered systems use encrypted, secure tether communications to prevent interception. A closed tether data link significantly reduces jamming risk, but physical security of the tether (to prevent an enemy physically cutting or damaging it) should also be addressed in training and planning.
Optimize Employment for Persistence and Coverage
Use tethered drones to complement other ISR assets by covering blind spots and maintaining eyes on target when other platforms must disengage. For example, if a satellite pass or high-altitude UAV has limited station time over a target, a tethered drone deployed forward can maintain surveillance before, during, and after that coverage window.
Commanders should allocate tethered UAVs to missions that require lengthy observation of a fixed area – such as stakeouts on an enemy position or protecting a flank – thereby freeing patrols or crewed aircraft for more dynamic tasks. This persistent use should be written into ISR collection plans. Additionally, coordinate between units so that tethered drones can hand off tracking of targets (one drone watching until it needs maintenance while another takes over) to ensure continuous coverage in critical situations.
Integrate into Communications Networks
Leverage tethered UAV systems not just as eyes but also as communication nodes. Doctrine should incorporate the dual-role nature of these systems – many tethered drones can carry communication relay payloads (antennas, radios) to extend line-of-sight radio and datalink range. For instance, in mountainous or urban terrain, a tethered drone hovering 60–100 meters up can connect platoons that are otherwise radio-separated by obstacles.
Plan for tethered UAVs to be deployed at command posts or key nodes to enhance C3 (command, control, communications) continuity. The U.S. Army’s requirements explicitly call for tethered UAVs to lengthen comms ranges for maneuver forces, so ISR planners should coordinate with signal officers on where a tethered drone could plug gaps in the communications architecture during operations.
This is especially relevant in NATO coalition settings, where a tethered drone might help link multinational force elements on a common network when standard infrastructure is lacking or disrupted.
Address Logistical and Security Considerations
Although tethered drones eliminate the need for constant battery resupply, they have their own support requirements. Commanders should ensure power sources (generators or vehicle power) are available and protected for tethered UAV operations. Position the ground station in defilade or under armor if possible (some designs allow control from inside a vehicle), to shield the crew and equipment.
Doctrine should also consider backup plans: for example, if the tether is severed or power fails, units should be prepared to either quickly recover the drone or have a secondary drone to deploy. In base defense scenarios, maintain at least two tethered UAV systems so one can take over if the other must be grounded for maintenance.
This redundancy and preparation need to be standard practice, much as having multiple observation posts or cameras would be for security. Additionally, include tethered UAV placement in force protection planning – while small, they could become targets if the enemy knows their value, so integrate them into air defense coverage (even a rifleman can guard the tethered drone’s airspace against small threats).
Training and Simulation with Tethered UAV Systems
Incorporate tethered UAV operations into training exercises and simulations at all levels. ISR units and regular combat units alike should drill on how to request, launch, recover, and exploit tethered drone feeds.
The goal is to build confidence in using the live intelligence from these systems for decision-making. Train analysts to treat tethered drone imagery with the same importance as reconnaissance patrol reports or spy plane imagery.
On the tactical side, practice quick emplacement of tethered drones during tactical pauses, and rehearse moving with tethered drones (for those designed to operate “on the move”). The more familiar troops are with the capabilities and limits (e.g. tether length, coverage area) of these systems, the more effectively they will be employed.
Doctrine should capture lessons from units that have already used tethered drones in exercises or real operations – for instance, adjusting the standard operating procedures on how high to fly for best resolution vs. covertness, or how to react if the tethered drone observes enemy activity (clear protocols for who gets the info and how to act on it).
By following these recommendations, military organizations can ensure that tethered UAVs are fully woven into the ISR fabric and operational doctrine, rather than being seen as niche gadgets. The result will be a more resilient and persistent ISR posture, able to cope with the demands of both modern high-tech warfare and enduring security missions.
Ultimately, tethered UAVs change the calculus of ISR by making persistent overhead surveillance available at the lowest echelon, on demand. Commanders who understand and exploit this capability will gain an edge in both planning and execution of operations. They will be able to maintain an unblinking eye on the battlefield or border, achieve better information dominance despite enemy jamming or stealth, and react faster to threats with confidence in the intelligence at hand.
As technology evolves, we can expect tethered drones to become more autonomous, lighter, and perhaps longer in reach – further increasing their doctrinal impact. But even with today’s systems, the message is clear: integrating tethered UAV systems into ISR doctrine enhances operational effectiveness, providing a persistent, secure, and watchful recon asset for the modern commander. The time has come for ISR planners to fully embrace this change, ensuring that the lessons from current conflicts inform a more resilient and innovative approach to reconnaissance and surveillance in the future.
Read our analysis on how Tethered Uavs are changing ISR doctrine, in the first par of this article: https://elistair.com/articles/how-tethered-uav-change-isr-doctrine/
Key references include official Army requirements for tethered UAS, field use cases documented by industry and military sources, and assessments of electronic warfare impacts on UAV operations.